Luckylinux's Self-Hosted Universe
Things I build. Things I host. Things I run.
A showcase of self-hosted applications, automation workflows, and cloud services—designed for privacy, control, and continuous learning
Development Tools
Powerful development and server management tools hosted on dedicated infrastructure
Code Server
Private AccessWeb-based VS Code instance for coding from anywhere—laptop, tablet, or smartphone—with full IDE features and secure remote access
Server Dashboard
Private AccessComprehensive control panel for managing services, monitoring system health, and accessing server terminal securely via browser interface on any device
Applications
Production-ready applications and services built from scratch
Railsplit
Helps you find confirmed train seats by intelligently splitting long journeys, finding efficient intermediate junctions, and suggesting routes with confirmed availability.
Portfolio
Complete showcase of my engineering projects, technical implementations, and development work
Services for Rent
Professional cloud services and automation tools available for your projects
Cloud Storage
As cheap as just Rs. 29/monthSecure, encrypted cloud storage with Google Drive-like features. Get your own private storage space with full privacy and control. Perfect for personal use.
n8n Workflows
at just Rs. 49/monthRent your own n8n member account for powerful workflow automation. Integrate 350+ services, automate tasks, and build custom workflows with an intuitive visual editor.
Web Analytics
Free ServiceFree privacy-focused analytics for your website. Track visitor metrics, device types and location data—all without cookies. Perfect alternative to Google Analytics.
Email Authentication
Free ServiceFree passwordless authentication for your website. Implement magic link email login in minutes. Secure, modern, and eliminates password management hassles for your users.
Server Infrastructure
Technical documentation of the self-hosted setup
Overview
This is a local self-hosted server used for learning, experimentation, and running real production services. The infrastructure provides hands-on experience with system administration, networking, and DevOps practices while serving actual applications to users.
Services are exposed securely to the internet using Cloudflare Tunnel without opening any inbound ports on the router or firewall. This eliminates the need for port forwarding and provides an additional layer of security through Cloudflare's edge network.
Architecture Overview
The request flow follows this path: Users → Cloudflare Edge → Cloudflare Tunnel → Nginx Reverse Proxy → Internal Services
Cloudflare acts as the public-facing endpoint, routing requests through an encrypted tunnel to the local server. Nginx then handles internal routing to appropriate services based on hostname and path.
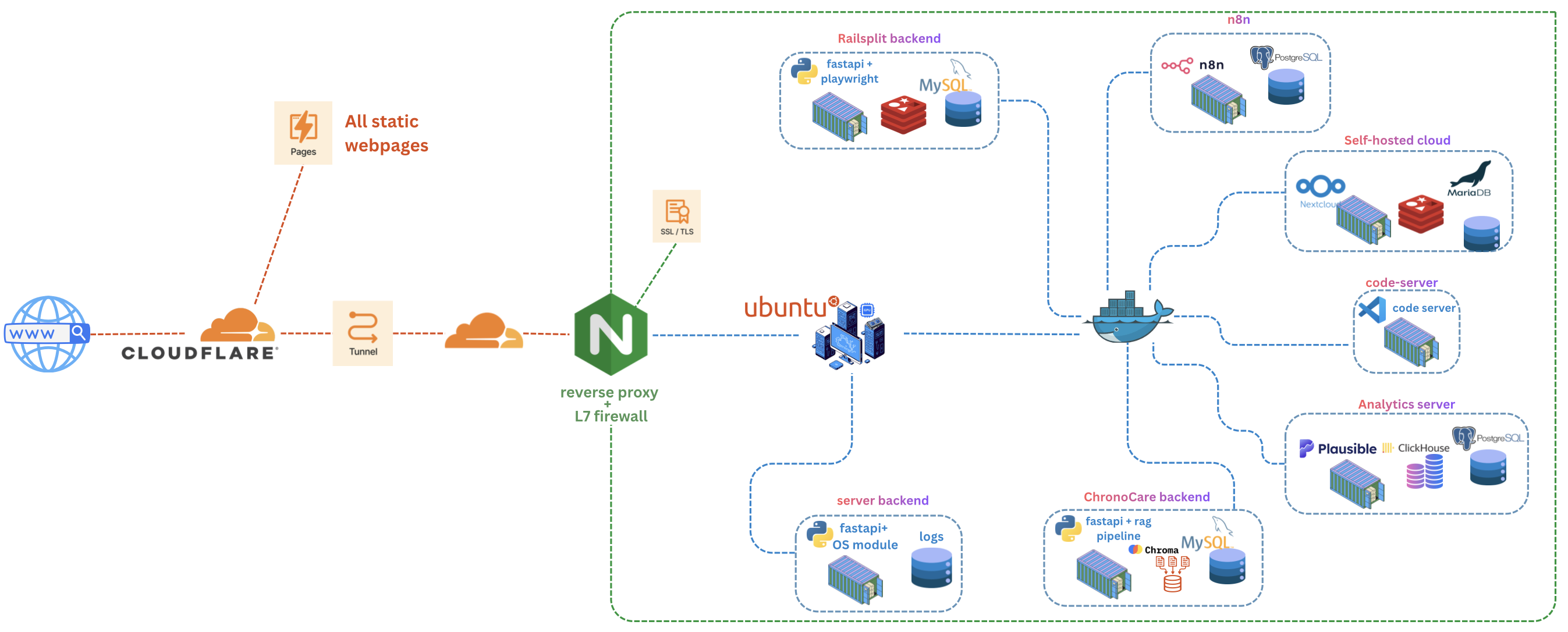
Networking & Exposure
Cloudflare Tunnel (cloudflared) is configured to map multiple subdomains to internal services. The tunnel daemon runs locally and maintains persistent connections to Cloudflare's edge network, eliminating the need for publicly exposed IP addresses or open inbound ports.
Most hostnames terminate at localhost:443, where Nginx handles reverse proxying based on the Host header. Some services connect directly to their specific ports for performance or compatibility reasons.
cloudflared Configuration (Simplified)
Note: This configuration is a real-world but sanitized example showing how subdomains are mapped to internal services.
ingress:
- hostname: server.luckylinux.dev
service: https://localhost:443
- hostname: railsplit-server.luckylinux.dev
service: http://127.0.0.1:3108
- hostname: n8n.luckylinux.dev
service: https://localhost:443
- hostname: chronocare-server.luckylinux.dev
service: http://127.0.0.1:3102
- hostname: code.luckylinux.dev
service: https://localhost:443
- hostname: analytics.luckylinux.dev
service: https://localhost:443
- hostname: ssh.luckylinux.dev
service: ssh://localhost:22 #(secured)
- hostname: openwisp2.luckylinux.dev
service: http://127.0.0.1:80
- hostname: cloud.luckylinux.dev
service: https://localhost:443
- service: http_status:404Internal routing to specific applications is handled by Nginx, not by cloudflared. The tunnel daemon simply forwards requests to the appropriate local port.
Nginx Reverse Proxy
Nginx acts as the single entry point for HTTPS traffic from the Cloudflare Tunnel. It routes requests to internal services and applications based on the Host header, enabling multiple services to share the same external port (443).
Example server block structure:
# Reverse proxy hardening (excerpt) server_tokens off; # Preserve real client IP from Cloudflare Tunnel real_ip_header CF-Connecting-IP; # Basic rate limiting limit_req_zone $binary_remote_addr zone=global:20m rate=10r/s; # TLS termination at Nginx (origin) ssl_protocols TLSv1.2 TLSv1.3; ssl_prefer_server_ciphers off;
TLS & Certificates
Cloudflare CA Origin Certificates are used to secure the connection between Cloudflare and the local server. Public TLS termination occurs at Cloudflare's edge, with origin certificates securing the tunnel-to-Nginx connection.
This setup provides end-to-end encryption: Browser → Cloudflare (public cert) → Tunnel (encrypted) → Nginx (origin cert) → Services
Services Hosted
The infrastructure currently hosts the following services:
- Nextcloud - Self-hosted cloud storage and collaboration platform
- n8n - Workflow automation and integration platform
- Plausible Analytics - Privacy-focused web analytics
- Code Server - Web-based VS Code instance
- Multiple custom applications - Frontend and backend services for various projects
All services run on a private internal network and are only accessible via the reverse proxy. Direct access to service ports is blocked by the host firewall.
Security Notes
- ✓No inbound ports exposed - All services are accessible only through Cloudflare Tunnel
- ✓Firewall enabled - Nginx L7 firewall& UFW configured to block unauthorized access to service ports
- ✓Internal service isolation - Services run in isolated containers with minimal privileges
- ✓TLS encryption - End-to-end encryption from browser to internal services
Why Self-Host?
Building infrastructure that prioritizes control, privacy, and continuous learning
Complete Infrastructure Control
Total ownership of the technology stack—from hardware to application layer—enabling custom configurations and unlimited scalability
Privacy by Design
Zero third-party data access with complete data sovereignty—no tracking, no external dependencies, absolute control over information
Engineering at Scale
Hands-on experience managing production-grade infrastructure, learning deployment patterns, monitoring, and optimization techniques
Production-Ready Systems
Real infrastructure handling live workloads and traffic—not sandbox demos, but systems built for reliability and performance